Hello guys !!! hope you all are doing well. Today i am going to shed some light on data security in Android.
First start with basic , what is data security or encryption in Android?
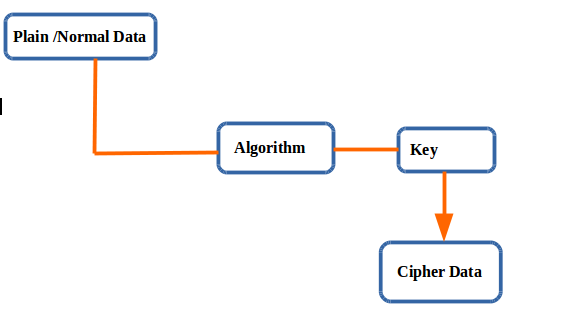
Hiding plain data with some sort of changed format by using algo with key to convert and retrieve data is called data encryption.
Here Plain data will be any data(personal, financial etc) without any sort of hiding. So that any user can easily accessed your data.
Of course everything works vice versa, if you have a cipher data and you know the algorithm and have a key, you will get original plain data with ease.
Algorithm Types
As we saw a very basic example of encryption. Nowadays algorithms are more complex and are separated on Symmetric and Asymmetric (there’s also a Hash Functions, that do not require a key, I will discuss it in later blog).
Stream cipher : — a symmetric encryption algorithm that processes the data a bit or a byte at a time with a key resulting in a randomized cipher data or plain data.
Block cipher :— deterministic algorithm operating on fixed-length groups of bits, called blocks. Block ciphers are important elementary components in the design of many cryptographic protocols, and are widely used to implement encryption of bulk data.
Modes & Paddings
Most common modes :-
Key Types
There are three key types:
First start with basic , what is data security or encryption in Android?
Hiding plain data with some sort of changed format by using algo with key to convert and retrieve data is called data encryption.
Here Plain data will be any data(personal, financial etc) without any sort of hiding. So that any user can easily accessed your data.
Of course everything works vice versa, if you have a cipher data and you know the algorithm and have a key, you will get original plain data with ease.
Algorithm Types
As we saw a very basic example of encryption. Nowadays algorithms are more complex and are separated on Symmetric and Asymmetric (there’s also a Hash Functions, that do not require a key, I will discuss it in later blog).
Symmetric : — the oldest and best-known technique.
- The encryption key and the decryption key are the same
- it is generally categorized as being either Stream Cipher or Block cipher
The most common Symmetric AES — the Advanced Encryption Standard (AES) is the algorithm trusted as the standard by the U.S. Government and numerous organizations.
Asymmetric :— a modern branch of cryptography.
- known as public-key cryptography in which the algorithms employ a pair of keys (a public key and a private key)
- use a different component of the pair for different steps of the algorithm
The most common Asymmetric algorithm is RSA — a public-key encryption algorithm and the standard for encrypting data sent over the internet.
Block cipher :— deterministic algorithm operating on fixed-length groups of bits, called blocks. Block ciphers are important elementary components in the design of many cryptographic protocols, and are widely used to implement encryption of bulk data.
Modes & Paddings
Block cipher has different Modes and Paddings that increases it protection level.
Modes : — a mode of operation describes how to repeatedly apply a cipher’s single-block operation to securely transform amounts of data larger than a block.
Padding : — block cipher works on units of a fixed size (known as a block size), but messages come in a variety of lengths. So some modes (namely ECB and CBC) require that the final block be padded before encryption.
Most common modes :-
ECB : — Electronic Codebook, the simplest of the encryption modes. The message is divided into blocks, and each block is encrypted separately.
CBC : — Cipher Block Chaining, each cipher data block depends on all plain data blocks processed up to that point. To make each message unique, an initialization vector must be used in the first block.
But simply because algorithm is not symmetric does not mean it can not have modes and paddings. Thats, for instance, RSA algorithm can be used with ECB mode and PKCS1Padding.
There are three key types:
- Secret key,
- Private key and
- Public key.
Secret key — a single secret key which is used in conventional symmetric encryption to encrypt and decrypt a message.
Private key — the secret component of a pair of cryptographic keys used for decryption in asymmetric cryptography.
Public key — The public component of a pair of cryptographic keys used for encryption in asymmetric cryptography.
Together Public and Private keys forms a public-private cryptographic Key Pair.
SecureRandom — generates cryptographically secure pseudo-random numbers. We will not use it directly in this series, but it is widely used inside of KeyGenerator, KeyPairGenerator components and Keys implementations.Private key — the secret component of a pair of cryptographic keys used for decryption in asymmetric cryptography.
Public key — The public component of a pair of cryptographic keys used for encryption in asymmetric cryptography.
Together Public and Private keys forms a public-private cryptographic Key Pair.
How Data security works in Android
Java Cryptography Architecture- Android data security builds on the Java Cryptography Architecture (JCA)
- In Android JCA provides API for digital signatures, certificates, encryption, keys generation and management
KeyPairGenerator — an engine class which is capable of generating a private key and its related public key utilizing the algorithm it was initialized with.
SecretKey — a secret (symmetric) key. The purpose of this interface is to group (and provide type safety for) all secret key interfaces (e.g., SecretKeySpec).
PrivateKey — a private (asymmetric) key. The purpose of this interface is to group (and provide type safety for) all private key interfaces(e.g., RSAPrivateKey).
PublicKey — a public key. This interface contains no methods or constants. It merely serves to group (and provide type safety for) all public key interfaces(e.g., RSAPublicKey).
KeyPair — this class is a simple holder for a key pair (a public key and a private key). It does not enforce any security, and, when initialized, should be treated like a PrivateKey.
KeyStore — database with a well secured mechanism of data protection, that is used to save, get and remove keys. Requires entrance password and passwords for each of the keys. In other words it is protected file that you need to create, read and update (with provided API).
Certificate — certificate used to validate and save asymmetric keys.
Cipher — provides access to implementations of cryptographic ciphers for encryption, decryption, wrapping, unwrapping and signing.
Provider — defines a set of extensible implementations, independent API’s. Providers are the groups of different Algorithms or their customizations. There are 3rd party providers, such as Bouncy Castle and Spongy Castle (android version of Bouncy Castle), as well as providers available out of box, such as cut-down version of Bouncy Castle (we will take a bit deeper look on them, later on, during this article).
Android Key Store
AndroidKeyStore was introduced in API level 18.
Feature of Android Key Store(AKS):-
- Lets you store cryptographic keys in a container to make it more difficult to extract from the device
- Once keys are in the key store, they can be used for cryptographic operations with the key material remaining non-exportable
- It offers facilities to restrict when and how keys can be used, such as requiring user authentication for key use or restricting keys to be used only in certain cryptographic modes
AndroidKeyStore is a JCA Provider implementation, where:
- No KeyStore passwords is required (really, at all)
- Key material never enters the application process
- Key material may be bound to the secure hardware (Trust Zone)
- Asymmetric keys are available from 18 +
- Symmetric keys are available from 23 +
Notes:-
- If device manufacture supports Trusted Execution Environment(TTE), your keys will be saved there (the most secure option);
- If device manufacture doesn’t support TTE, keys will be stored in emulated software environment, provided by the system.
- In both cases, your keys will be automatically removed from the system after deleting the application.
Also keys material is never exposed, even to us (we will see this later on). We will just work with key references, that is passed to KeyStore System Service, where, under the cover, all dirty work with key materials is done .
Sample Project
In this project we will save user Secrets, locally, and keep them protected using Encryption, Fingerprint and Confirm Credentials API’s.
User creates a master password (during sign up process). This password will be used to protect Secrets: to add new, view, edit and delete already created Secrets, user needs to enter master password.
What is Secret ? Anything user want to kept protected: gmail password, credit card pin code
Download Sample Code from Github(coming soon)
In Next Blog I will discuss Lock Screen, Choose a Key, Key Storage, Key Generation, Key Management, Encryption & Decryption, Usage Example
In this project we will save user Secrets, locally, and keep them protected using Encryption, Fingerprint and Confirm Credentials API’s.
User creates a master password (during sign up process). This password will be used to protect Secrets: to add new, view, edit and delete already created Secrets, user needs to enter master password.
What is Secret ? Anything user want to kept protected: gmail password, credit card pin code
Download Sample Code from Github(coming soon)
In Next Blog I will discuss Lock Screen, Choose a Key, Key Storage, Key Generation, Key Management, Encryption & Decryption, Usage Example
Thanks
Happy Coding!!!!